KLINGE DATA SECURITY STATEMENT |
|
Overview
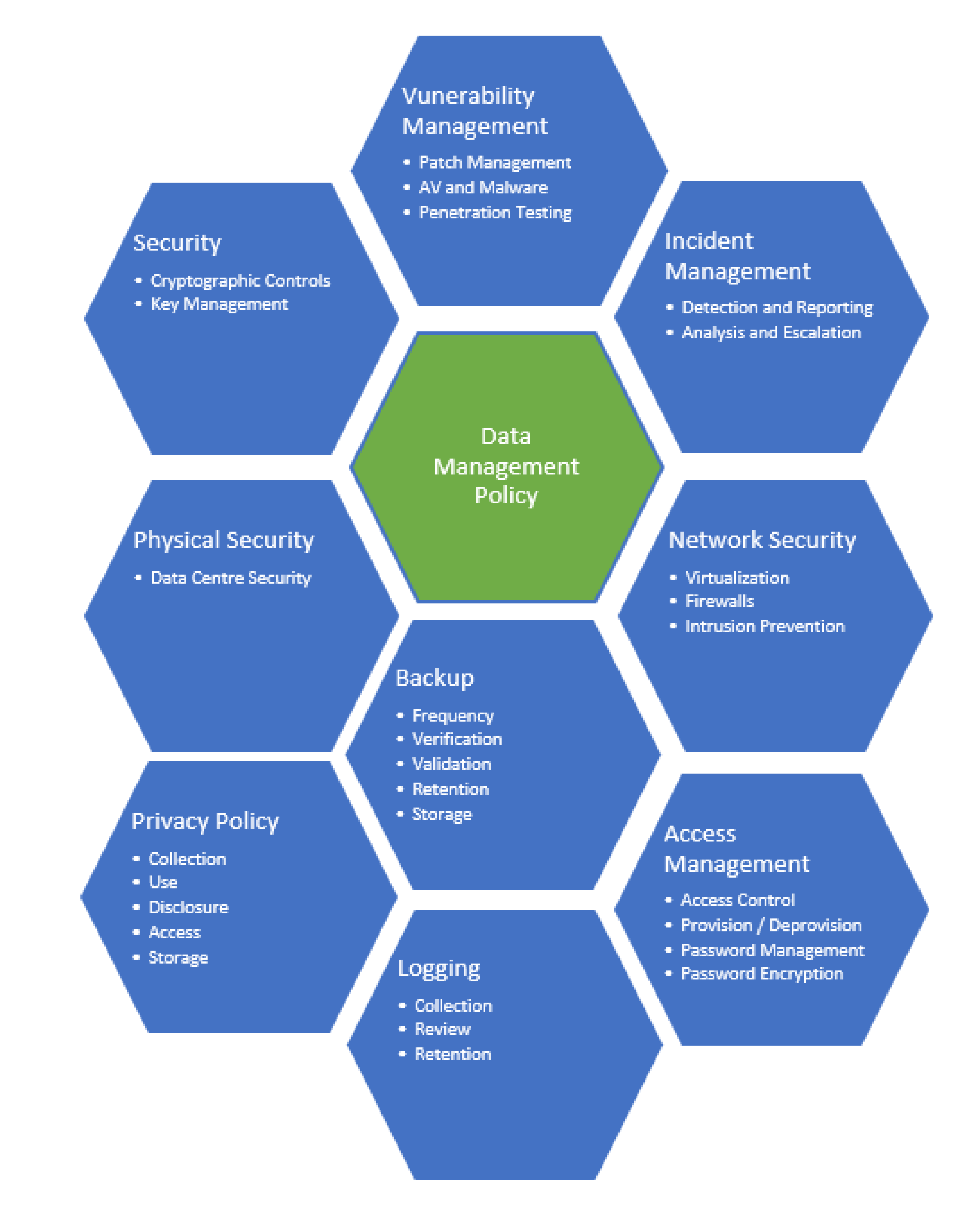
At KLINGE we are aware of the ever increasing threat to data security from criminal cyber attacks where commercial and personally identifiable information (PII) may be at risk of disclosure or ransom. KLINGE Tyre Management Systems (TMS) do not require data generally accepted as PII. To mitigate risk regarding hosted TMS data, KLINGE follows a Data Management Policy (DMP). The DMP covers topics as outlines in the infographic below.
Data Management Policy
Klinge TMS Products
KLINGE offers TMS products as Total Tyre Control Earthmover and Total Tyre Control Web. The Total Tyre Control Earthmover product is offered as an on-premises deployment or as a KLINGE hosted virtualized application. Total Tyre Control Web is offered as a KLINGE managed web application. Users of Total Tyre Control Earthmover in an on-premises deployment are responsible for their own data management strategies, although options exist to setup automated backup of data to the KLINGE cloud.
DMP Implementation
Backup
The implementation of the DMP can vary between hosting environments however the controls remain the same. For example lets discuss Data Backup in general. All client TMS data is backed up at least daily. Retention varies depending on the backup source however it is generally accepted that data is kept at least 4 weeks. All Backup data is encrypted at rest and during transmission where it is stored in an AWS S3 repository providing dual redundancy.
Security
Data in Transit. Where clients access a Total Tyre Control product via a compliant web browser they can be assured that traffic across the internet is secured via HTTPS using SSL certificates and TLS 1.2 or better.
Physical Security
Within geographic constraints KLINGE uses reputable providers of industry accepted data centres. Currently all KLINGE data hosting services are provided by Amazon Web Services (AWS).
Privacy Policy
KLINGE does provide a service that allows Tyre and Rim manufacturers to view specifically filtered TMS data. Be assured KLINGE will never share your TMS data with any other third party without your express permission.
Vulnerability Management
KLINGE is ever vigilant to ensure servers are correctly patched against security vulnerabilities and that AV and Malware detection software is installed on all servers. We accomplish this through scheduled patching, review of server logs and 3rd party verification of key vulnerabilities such as scheduled penetration tests.
Logging
KLINGE has monitoring software on all servers that provide alerts to logging exceptions. Monitoring also extends to server contact and stress exceptions.
Incident Management
In the event that KLINGE becomes aware of a security incident KLINGE will contact any affected clients with disclosure of the incident details and will disclose incidents based on governing laws and regulations in relative jurisdictions.
Network Security
KLINGE employs intrusion prevention at the appliance level on its firewall. Network security is further enhanced through AWS firewalling limiting connection protocols to the public interfaces.
Access Management
KLINGE ensures that access to its hosted resources is limited to employees on a needs basis. KLINGE is in the process of employing Multi Factor Authentication (MFA) or Single Sign On (SSO) as part of its access management company wide. This allows for increased security at logon but also in deprovisioning user access. KLINGE can currently offer SSO to clients of Total Tyre Control Earthmover and hopes to soon include MFA or SSO to its TTC Web product.
Conclusion
If you have any specific questions about KLINGE’s Security Policies please feel free to contact us via one of our support channels ttc.support@klinge.com.au
